API Security Best Practices
This explainer highlights important security practices that everyone should try to implement to reduce the risk of unauthorized access and potential security threats for APIs.
Intro
API security is paramount in today's digital landscape. APIs (Application Programming Interfaces) enable seamless interactions between applications and services. As APIs expose endpoints for accessing resources and data, they also present security challenges that must be addressed.
To ensure the integrity, confidentiality, and availability of APIs and the data they access, following best practices for API security is essential. These practices encompass authentication, authorization, input validation, encryption, monitoring, and logging. By implementing these best practices, organizations can mitigate risks and protect their APIs from security threats.
Venly-API Specific Security Practices
Securely Store Access Credentials
Securely storing API keys, tokens, and other credentials is essential to prevent unauthorized access and protect sensitive information. Hardcoding credentials in your application code or storing them in insecure locations can lead to security vulnerabilities.
Similarly, you need to safely secure the Venly API access credentials (Client ID + Client Secret) that are obtained from the Portal. These access credentials are used to obtain the bearer token required to authenticate all API calls. If the credentials fall into the wrong hands, your app is at risk of security threats.
Use a secure method, such as a password manager, to store your access credentials. Avoid storing them in plain text or in easily accessible locations. Only share access credentials with authorized personnel and ensure they are aware of the importance of keeping them secure.
Make sure you know the trails of who has access to these credentials and when they access it. You can also create an audit trail to keep track of the people and time when the credentials are accessed.
Implementation: Use secure storage mechanisms such as environment variables, configuration files with restricted access, or secure vault services to store credentials securely.
Attack Mode
Attack mode can be activated/deactivated from the authentication section of the portal.
Attack Mode is a critical security feature designed to safeguard your platform against potential security threats and unauthorized access. By activating Attack Mode, you can instantly halt all incoming traffic from your clients or servers to our system, ensuring your data and operations remain secure during a security incident.
Knowing that you have a reliable mechanism to stop potential threats allows you to respond confidently to security incidents. With a simple toggle, you can activate Attack Mode and ensure your system is protected.
Hacking Attempts: If you suspect that your platform is under a hacking attempt, enabling Attack Mode can provide immediate protection by blocking all incoming connections.
Security Breaches: In the event of a security breach, quickly activating Attack Mode helps contain the threat and prevent further unauthorized access.
Activating Attack Mode will temporarily stop all incoming traffic, which may cause a disruption in service. Use this feature diligently and inform your users if necessary.
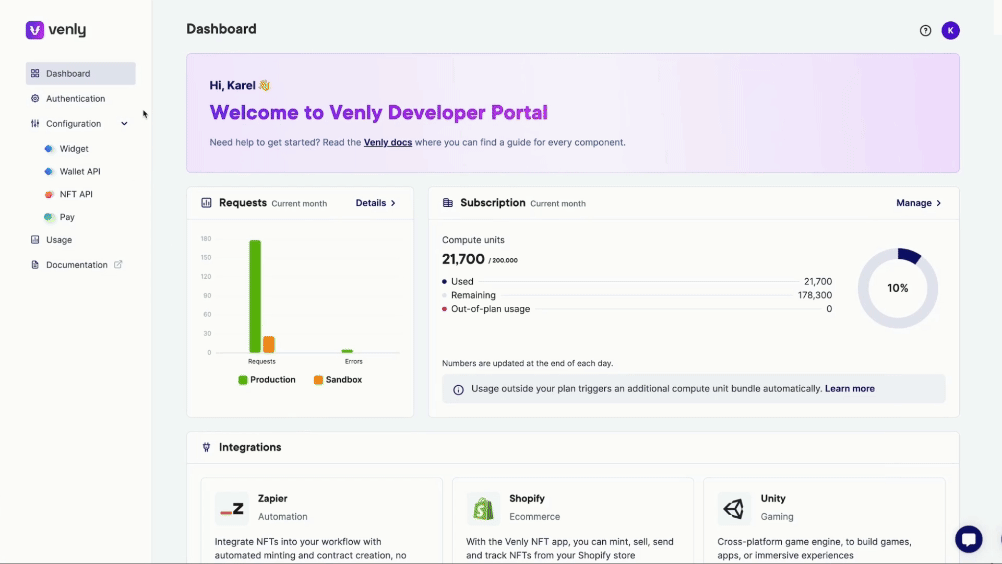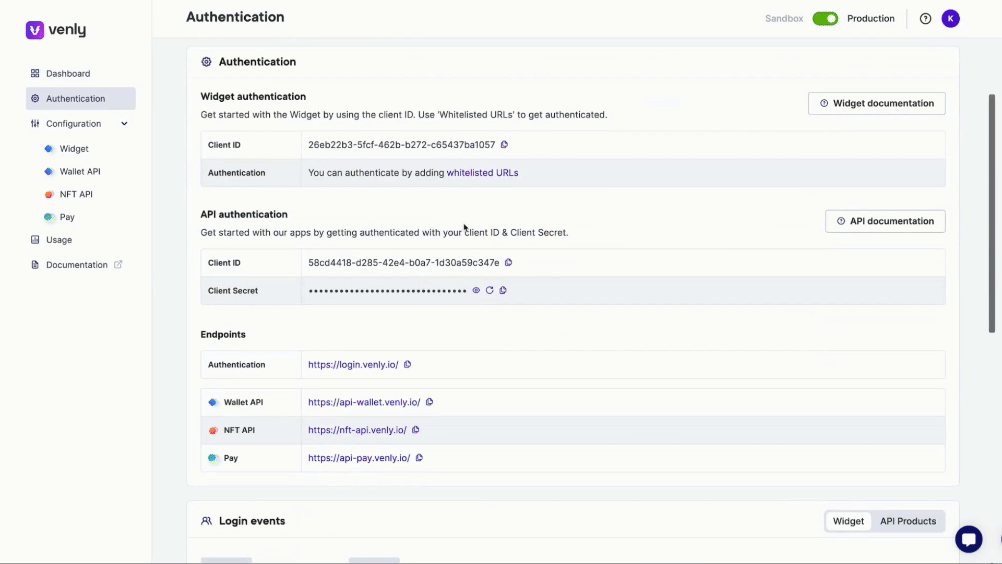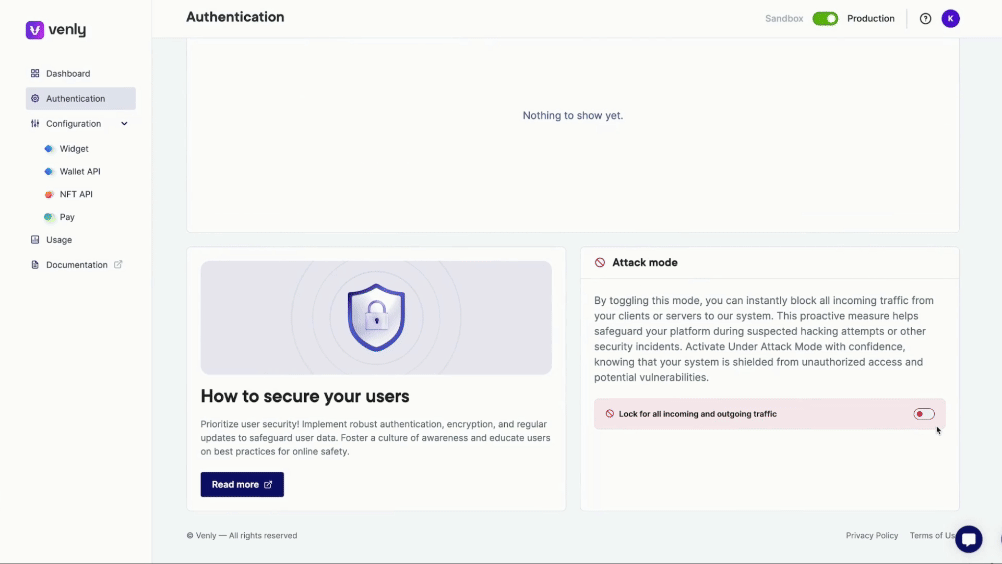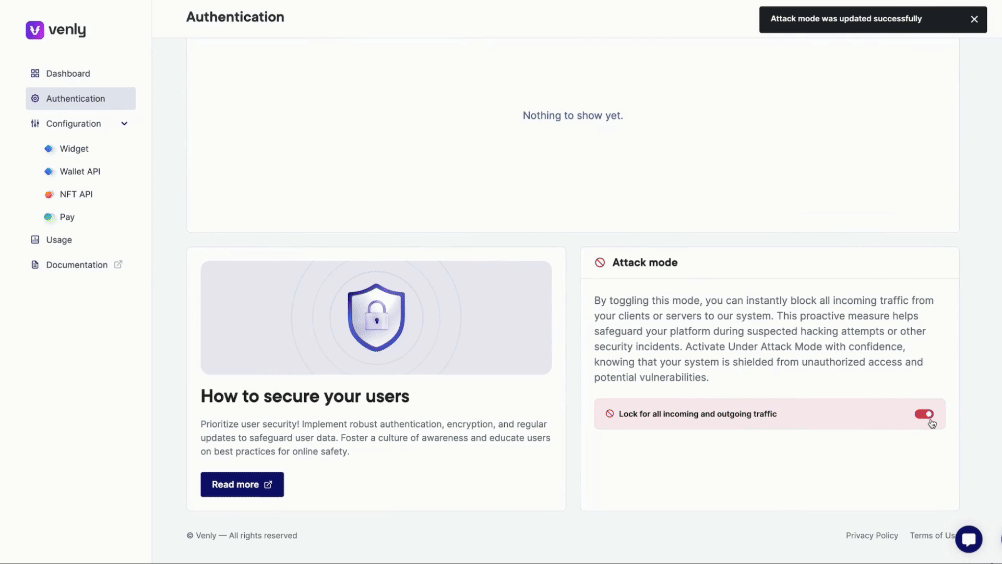
Attack Mode to stop incoming traffic from your servers
Create Emergency Code as Backup
We highly recommend that you provide your end-users with an emergency code signing method along with a PIN signing method. This ensures that they have a backup means of accessing their wallets or recovering their signing method if they lose their PIN.
Read more about signing methods.
Implementation: Generate the emergency code for each user that can be used to access their wallets in case they forget their PIN. This code is advised to be stored securely and only accessible to your end-user.
Learn how to create emergency code for your end-users.
General API Security Practices
Authentication
Authentication in terms of API security refers to verifying the identity of a client application or user accessing an API. It ensures that only authorized entities can access the API and its resources.
Authentication mechanisms commonly used in API security include:
- API Keys: Unique identifiers issued to clients to authenticate their requests to the API.
- OAuth: An authorization framework that allows a client application to access resources on behalf of a user.
- JWT (JSON Web Tokens) is a compact, URL-safe means of representing claims that can be securely transferred between two parties.
Venly uses OAuth + JWT authorization for its APIs.
Importance: Strong authentication mechanisms like OAuth, API keys, or JWT tokens ensure that only legitimate users or applications can access your API, protecting sensitive data and resources from unauthorized access.
Implementation: Using OAuth tokens to authenticate users before allowing access to the API's resources.
Risks of Not Implementing: Without solid authentication, your API is susceptible to unauthorized access, leading to data breaches, misuse of resources, and potential legal consequences for failing to protect user data.
Authorization
Authorization, in terms of API security, refers to the process of determining what actions a user or application is allowed to perform on an API. It involves verifying the user or application's identity and checking whether they have the necessary permissions to access or manipulate the requested resources.
Authorization is typically implemented using access control mechanisms, such as role-based access control (RBAC) or attribute-based access control (ABAC). RBAC assigns roles to users or applications and grants permissions based on these roles. On the other hand, ABAC uses attributes of the user or request (such as user roles, time of day, or location) to determine access rights.
Authorization helps ensure that only authorized users or applications can access sensitive data or functionality.
Importance: Implementing strict access control ensures that users or applications have the minimum necessary access to resources, reducing the risk of data breaches and ensuring compliance with security policies and regulations.
Implementation: Using role-based access control (RBAC) to grant permissions to users based on their roles, limiting access to sensitive resources.
Risks of Not Implementing: Lack of proper authorization can result in unauthorized access to sensitive data or functionalities, leading to data leaks, compliance violations, and reputational damage.
Input Validation
Input validation in terms of API security refers to validating and sanitizing all input data received by an API to prevent malicious attacks, such as injection attacks (e.g., SQL injection, cross-site scripting).
It involves checking input data against predefined rules (e.g., data type, length, format) to ensure it meets the expected criteria. This helps protect the API from receiving and processing malicious or malformed input that could be used to exploit vulnerabilities and compromise the system's security.
Importance: Validating and sanitizing input data helps prevent injection attacks such as SQL injection and cross-site scripting (XSS), which can lead to data loss, unauthorized access, and compromise of sensitive information.
Implementation: Validating input data to prevent SQL injection attacks, ensuring that only safe data is processed by the API.
Risks of Not Implementing: Without proper input validation, attackers can exploit vulnerabilities in your API to execute malicious code, steal sensitive information, and disrupt services, compromising the integrity and security of your application.
Rate Limiting
Rate limiting is a security measure used to control the rate of requests that clients can make to an API within a specific timeframe. It helps prevent API abuse by limiting the number of requests a client can make, thus protecting the API from being overwhelmed by a large number of requests or targeted denial-of-service (DoS) attacks.
By implementing rate limiting, API providers can ensure fair resource usage, prevent unauthorized access, and protect against API abuse. Rate limiting can be based on various factors, such as the number of requests per second, minute, or hour, the client's IP address, or the authentication token used by the client.
Importance: Implementing rate limiting prevents abuse of your API by restricting the number of requests a user or application can make within a specific timeframe, protecting against denial-of-service (DoS) attacks, and ensuring fair resource usage.
Implementation: Limiting the number of requests a client can make to the API within a specific timeframe to prevent abuse and ensure fair usage.
Risks of Not Implementing: Without rate limiting, your API is vulnerable to abuse, leading to increased costs, degraded performance, and potential service disruptions for legitimate users.
Encryption
Encryption in API security refers to encoding data transmitted between clients and the API server to protect it from unauthorized access and interception. By encrypting data, sensitive information such as user credentials, access tokens, and other sensitive data is transformed into a secure format that can only be decoded by authorized parties with the correct decryption key.
Encryption helps ensure the confidentiality and integrity of data transmitted over the API, protecting it from eavesdropping, tampering, and unauthorized access. It is typically implemented using Transport Layer Security (TLS), which encrypts data in transit or encrypts data at rest to protect it while stored on the server.
Importance: Encrypting data in transit with Transport Layer Security (TLS) protects against eavesdropping and ensures data integrity and confidentiality, safeguarding sensitive information from unauthorized access.
Implementation: Encrypting data transmitted between clients and the API server using TLS to protect it from unauthorized access.
Risks of Not Implementing: Without encryption, data transmitted over your API can be intercepted by attackers, leading to unauthorized access, data breaches, and compliance violations, exposing your organization to financial and reputational damage.
Web Application Firewall (WAF)
Using a Web Application Firewall (WAF) is critical to API security, as it helps protect your application from common web-based attacks. A WAF sits between the client and the server and analyzes HTTP requests and responses to filter out malicious traffic. It can detect and block various types of attacks, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) before they reach your API.
Importance: One of the key advantages of using a WAF is its ability to provide a layer of defense against known vulnerabilities and zero-day attacks. WAFs can be configured to block requests that match known attack patterns or to inspect requests for suspicious behavior. This proactive approach can help protect your API from new and emerging threats.
Implementation: Deploying a Web Application Firewall (WAF) in front of a web application creates a protective barrier between the application and the Internet. A WAF acts as a reverse proxy rather than a proxy server, which shields a client machine's identity using an intermediary. It safeguards the server from exposure by requiring clients to pass through the WAF before reaching the server.
Risks of Not Implementing: Without a WAF, web applications are more susceptible to common web-based attacks such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). Zero-day attacks, which exploit previously unknown vulnerabilities, pose a significant threat to web applications. A WAF can help mitigate these risks by providing virtual patching and protection against emerging threats. Without a WAF, web applications are more exposed to such attacks.
Monitoring and Logging
Monitoring and logging help you identify abnormal patterns or suspicious activity, such as unauthorized access attempts or unusual traffic spikes, enabling you to mitigate potential threats proactively. Implementing monitoring and logging involves using tools and services to track API usage, analyze logs, and generate alerts for suspicious activity. This lets you quickly respond to security incidents and protect your API and data.
Importance: Monitoring API usage and logs for suspicious activity allows you to detect and respond to security incidents promptly, reducing the impact of breaches and ensuring compliance with security policies and regulations.
Implementation: An API provider uses logging to record all incoming requests, including IP addresses and request payloads. Monitoring tools analyze these logs for unusual patterns that may indicate a security threat.
Risks of Not Implementing: Monitoring and logging is necessary for you to be aware of security incidents or breaches, allowing attackers to persist undetected and causing more significant damage to your organization's reputation.
Error Handling
Error handling in API security refers to managing and responding to errors during API interactions. Proper error handling is essential for maintaining an API's security and integrity. It involves providing users with informative but generic error messages to prevent the leakage of sensitive information about the API's internals.
Error handling is essential for API security because:
- It helps prevent the exposure of sensitive information, such as database schema or system internals, that attackers could exploit.
- It reduces the risk of attackers gaining insights into the API's security mechanisms and potentially exploiting vulnerabilities.
- It ensures that users receive clear and actionable error messages, improving the overall user experience and reducing the likelihood of security incidents caused by user confusion or frustration.
Importance: Implementing proper error handling prevents leaking sensitive information and helps maintain the security and integrity of your API by providing informative but generic error messages to users.
Implementation: An API returns a generic error message "Internal Server Error" when encountering an unexpected error. This prevents attackers from gaining insights into the API's internals.
Risks of Not Implementing: Inadequate error handling can expose sensitive information about your API's internals, providing attackers with insights to exploit vulnerabilities and potentially leading to data breaches or service disruptions.
Content-Type Checking
Content-type checking in API security means validating that requests and responses sent to and from an API have the correct content types. This helps prevent certain types of attacks, such as cross-site scripting (XSS) and cross-site request forgery (CSRF), by ensuring that data is interpreted correctly and securely.
For example, suppose an API expects JSON data in a request. In that case, it should verify that the Content-Type header of the request is set to "application/json." Similarly, when returning a response, the API should set the Content-Type header to indicate the type of data being returned, such as "application/json" for JSON data.
Importance: Ensuring that requests and responses have the correct content types prevents attacks like XSS and CSRF and ensures that data is interpreted correctly and securely.
Implementation: An API endpoint expects JSON data in the request body. If a request with a different content type is received, the API responds with a 415 status code, indicating that the request is not supported.
Risks of Not Implementing: Without content-type checking, your API is vulnerable to attacks that can manipulate or execute malicious content, leading to data breaches, security vulnerabilities, and potential legal consequences for failing to protect user data.
API Gateway
Using an API gateway to manage and secure your API endpoints provides an additional layer of security. API gateways can enforce authentication and authorization, perform rate limiting and content validation, and provide logging and monitoring capabilities, helping you secure your API against various threats.
Importance: Using an API gateway to manage and secure your API endpoints provides an additional layer of security by enforcing authentication, authorization, rate limiting, and other security policies.
Implementation: An organization uses an API gateway to manage access to its internal APIs. The gateway enforces authentication, rate limiting, and content validation policies before forwarding requests to the backend APIs.
Risks of Not Implementing: Without an API gateway, your API is exposed to various security threats, including unauthorized access, data breaches, and service disruptions, compromising the security and integrity of your API and data.
IP Allowlisting
IP allowlisting is a security measure that restricts access to an API to a specific list of IP addresses. Only requests originating from these allowlisted IP addresses can access the API, while requests from other IP addresses are blocked. This helps enhance API security by limiting access to trusted entities and reducing the risk of unauthorized access and potential security threats.
Importance: IP allowlisting allows you to restrict access to your API to a predefined list of IP addresses, providing an additional layer of security by ensuring that only authorized clients can access your API.
Implementation: A company's API is only accessible from specific IP addresses corresponding to its partner organizations. The firewall blocks requests from other IP addresses, ensuring that only authorized partners can access the API.
Risks of Not Implementing: Without IP allowlisting, your API is exposed to unauthorized access from any IP address, increasing the risk of unauthorized access, data breaches, and misuse of resources.
Bounty Programs
We also recommend launching a bounty program to identify and address vulnerabilities in your software processes and applications. By incentivizing security researchers and ethical hackers to find and report vulnerabilities, they can proactively improve security and protect your customers' data.
A bounty program not only helps you discover and fix security issues but also enhances your reputation as a company committed to security. It's an effective way to leverage the expertise of the broader security community and stay ahead of potential threats.
Updated 4 months ago