Self-Custody Infrastructure
Be the owner of your funds without compromising speed and security using Venlys' self-custody infrastructure
Venlys' Self-Custody Infrastructure is a secure and reliable process to store your digital assets in secure digital wallets. With our robust APIs and multi-layer security, you can rely on our work to keep your assets safe and accessible.
How do we do it at Venly?
Web Authentication Service
Venly utilizes an identity provider and web authentication service as the initial layer of authentication. Users can authenticate using their email and password or via a social login, acquiring access to the developer portal. Clients' requests to Venly (web, browser extension, or mobile) must first be authenticated to gain access to credentials via the developer portal.
Authentication via a Bearer token
Next, the user must obtain a bearer token using their access credentials. The access credentials (Client ID and Client Secret), are obtained from the authentication section of the developer portal. The bearer token is the user's entry for using API calls.
- The bearer token is only valid for six minutes and must be refreshed to obtain a new one.* Learn how to authenticate with Venly services.
Signing Methods
To this end, we implement an additional authorization layer called signing methods. These signing methods are only known to end-users and are used to unlock their wallets.
Every sensitive operation (for example, signing a transaction, initiating a transaction, or exporting a wallet) requires the end-user to authorize the request to perform that operation using their signing method.
We allow three types of signing methods:
- PIN: A six-digit pincode only known by the end-user.
- Emergency Code: A complex password that serves as a gateway to unlock a wallet or recover a lost PIN. It is 25 characters long and has a minimum of 128 bits of entropy.
- Bimoterics: This signing method allows users to utilize biometric features such as Face ID or Touch ID for authentication.
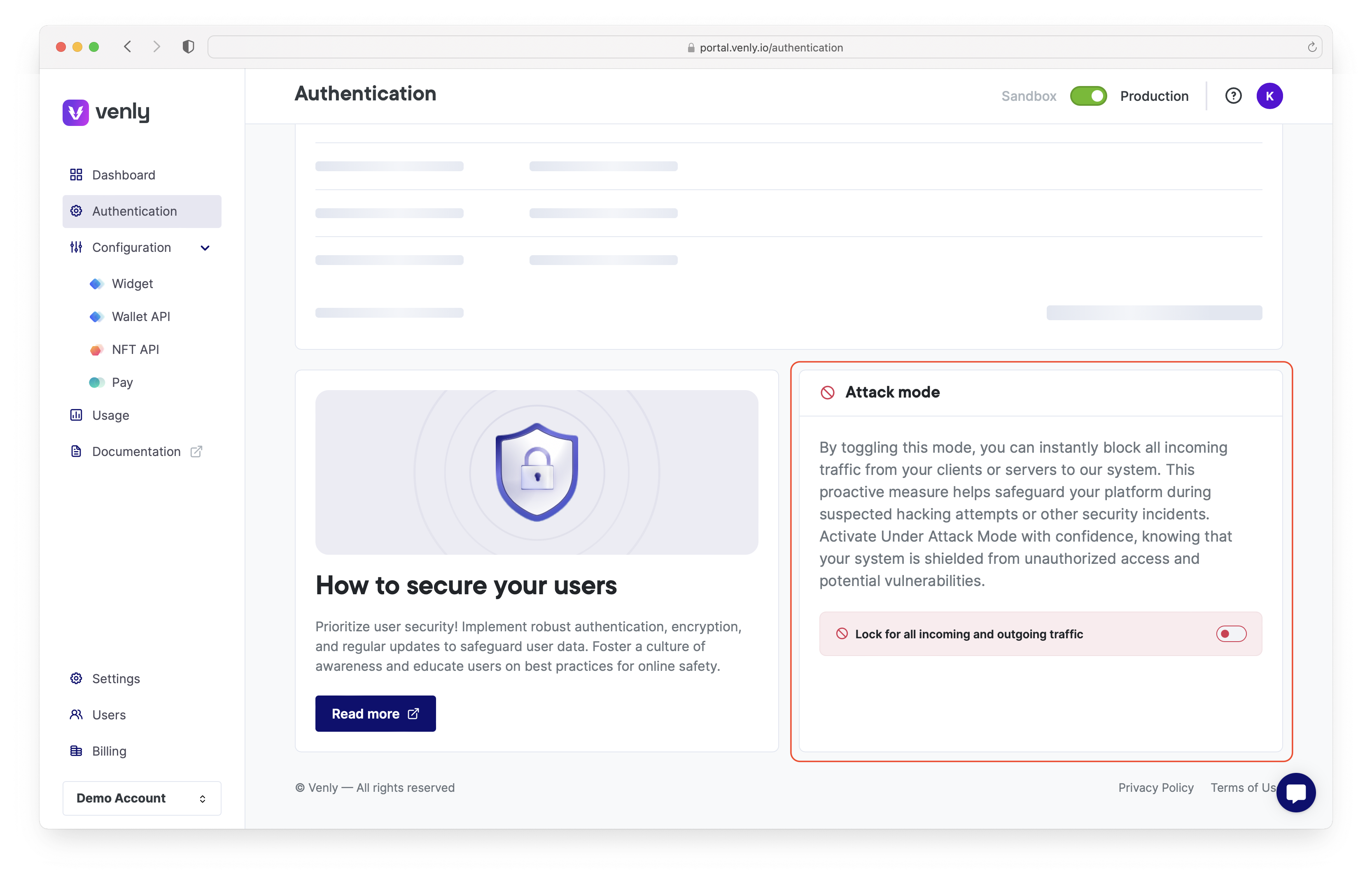
Attack Mode
Attack mode can be activated/deactivated from the authentication section of the portal.
Attack Mode is a critical security feature designed to safeguard your platform against potential security threats and unauthorized access. By activating Attack Mode, you can instantly halt all incoming traffic from your clients or servers to our system, ensuring your data and operations remain secure during a security incident.
Knowing that you have a reliable mechanism to stop potential threats allows you to respond confidently to security incidents. With a simple toggle, you can activate Attack Mode and ensure your system is protected.
Hacking Attempts: If you suspect that your platform is under a hacking attempt, enabling Attack Mode can provide immediate protection by blocking all incoming connections.
Security Breaches: In the event of a security breach, quickly activating Attack Mode helps contain the threat and prevent further unauthorized access.
Activating Attack Mode will temporarily stop all incoming traffic, which may cause a disruption in service. Use this feature diligently and inform your users if necessary.
Login Events
The Login Events feature allows you to monitor and track every instance where your access credentials are used to authenticate with Venly. By keeping a close eye on this section, you can ensure that only authorized logins occur, providing an additional layer of security for your account.
Date and Time: Each login event is recorded with the precise date and time, allowing you to verify the exact moment your credentials were used.
IP Address: The IP address associated with each login attempt is logged, helping you identify the location of the access.
Visit the authentication section of the portal and check the date, time, and IP address of each login event. Ensure that all logins are from recognized IP addresses and expected times. Look for any login attempts from unknown IP addresses or at unusual times. These could indicate potential security issues.
Shamir's secret sharing
A wallet's private key is divided into two shares: user-owned share and application share. These shares are further encrypted and stored in a key vault.
The user-owned share can be decrypted using that user's signing method. The application share is decrypted using the credentials: client ID and client secret.
Both of these shares are combined and unlock an end user's wallet. If a malicious entity gains access to one of the two shares, it is practically useless for them, as both shares must be combined to gain access to a wallet.
Isolated generation of the private key
Venly uses Amazon Fargate to generate the private key of a wallet when required temporarily. With the Fargate launch type, you package your application into containers and specify how much CPU power and memory it needs. You also set up networking and security rules. Each Fargate task runs in its own isolated environment, meaning it doesn't share its core resources—like CPU, memory, or network connection—with any other task. This ensures your application runs isolated and secure.
Segregated Model
Venly's offerings, namely the Wallet-API and Widget solutions, follow a segregated model, reflecting a commitment to providing users with a high level of individual control, security, and transparency in managing their digital assets.
Each user is treated as a separate and unique entity. Tokens are not pooled together, and the wallet's owner is the sole custodian of that wallet.
Under Venly's segregated accounts model, each user becomes the sole custodian of their wallet. This means that the ownership and control of the wallet's private keys rest entirely with the individual user.
Clean and simple integration
Our service offerings are designed for easy implementation and seamless integration with your applications. We understand that an easy integration process is key to minimizing issues and maximizing efficiency. On the other hand, more complex integrations, such as the one required for MPC (Multi-Party Computation), can lead to increased challenges and potential vulnerabilities.
While MPC offers advanced security features, its integration process can be more involved, potentially leading to compatibility issues or vulnerabilities like the Zero Day vulnerability
Proven Security
Venly boasts an impressive six-year track record of impeccable security, having never experienced a single security breach since its inception.
With over 6 million wallets powered by Venly, our commitment to safeguarding users' assets underscores our reliability and trustworthiness in the ever-evolving digital landscape.
Venly's unwavering dedication to security has ensured that user wallets remain uncompromised, maintaining our impeccable track record in the industry.
SOC 2 Type II Certification
Venly, the leading blockchain technology solutions provider, is pleased to announce that it has successfully completed the Service Organization Control 2 (SOC 2) Type 2 compliance assessment. This achievement reflects Venly's dedication to upholding its services' highest data security, privacy, and reliability standards.
By achieving SOC 2 Type II compliance, Venly demonstrates its proactive approach to safeguarding customer data and confidential information. The rigorous assessment process involved a comprehensive evaluation of Venly's systems, policies, and procedures, ensuring they meet the strictest industry standards.
Cobalt.io Audits
We at Venly quickly identify and reduce risk with Audits performed by Cobalt.io. They offer instant access to expert testers and real-time security findings. We seamlessly scale our security efforts as needs change. We stay ahead of threats with continuous offensive security testing, relying on seasoned experts to safeguard our organization. As a reliable partner, Cobalt combines expert insights to carry out detailed audits of security.
Bug Bounty Program
We also offer a bug bounty program via Intigriti - (cybersecurity bug bounty program). By leveraging the skills of a diverse pool of ethical hackers, we can identify and address vulnerabilities more effectively than relying solely on our internal team.
With a bug bounty program, our systems are continuously tested, ensuring that new vulnerabilities are identified and resolved promptly. The insights gained from bug reports lead to better code quality and more secure product development practices.
Encrypted Databases
Within Venly's framework, encryption isn't just an afterthought; it's a foundational principle of operations. Each piece of data stored within the databases is encrypted using robust encryption algorithms, rendering it indecipherable to anyone without the proper cryptographic keys.
This approach ensures that even if a malicious actor were to gain access to the database, the information would remain safely locked away, beyond their reach.
ISO27001 Certification
Venly has received its official ISO 27001 certification, the world’s best-known standard for information security management systems.
Being so certified “proves that we have consistently implemented rigorous controls,” commented Venly CEO Tim Dierckxsens, “and demonstrates our dedication to maintaining the highest security and compliance standards.”
These standards comprise a systematic approach to managing sensitive information and reducing the risk of security breaches. They provide best practices in:
- Risk assessment and management
- Access control and user management
- Incident management and response
- Business continuity planning
- Compliance with legal and regulatory requirements
- Physical and environmental security
Enterprise-grade Security
Updated 4 months ago